Description
1) What is phishing?
Phishing is a social-engineering attack where criminals trick you into revealing credentials, mobile-money one-time codes, or sensitive files. They impersonate trusted brands (banks, telecoms, government, NGOs, or colleagues) via email, SMS, WhatsApp/Telegram, phone calls, or fake websites.
2) How phishing works (in plain language)
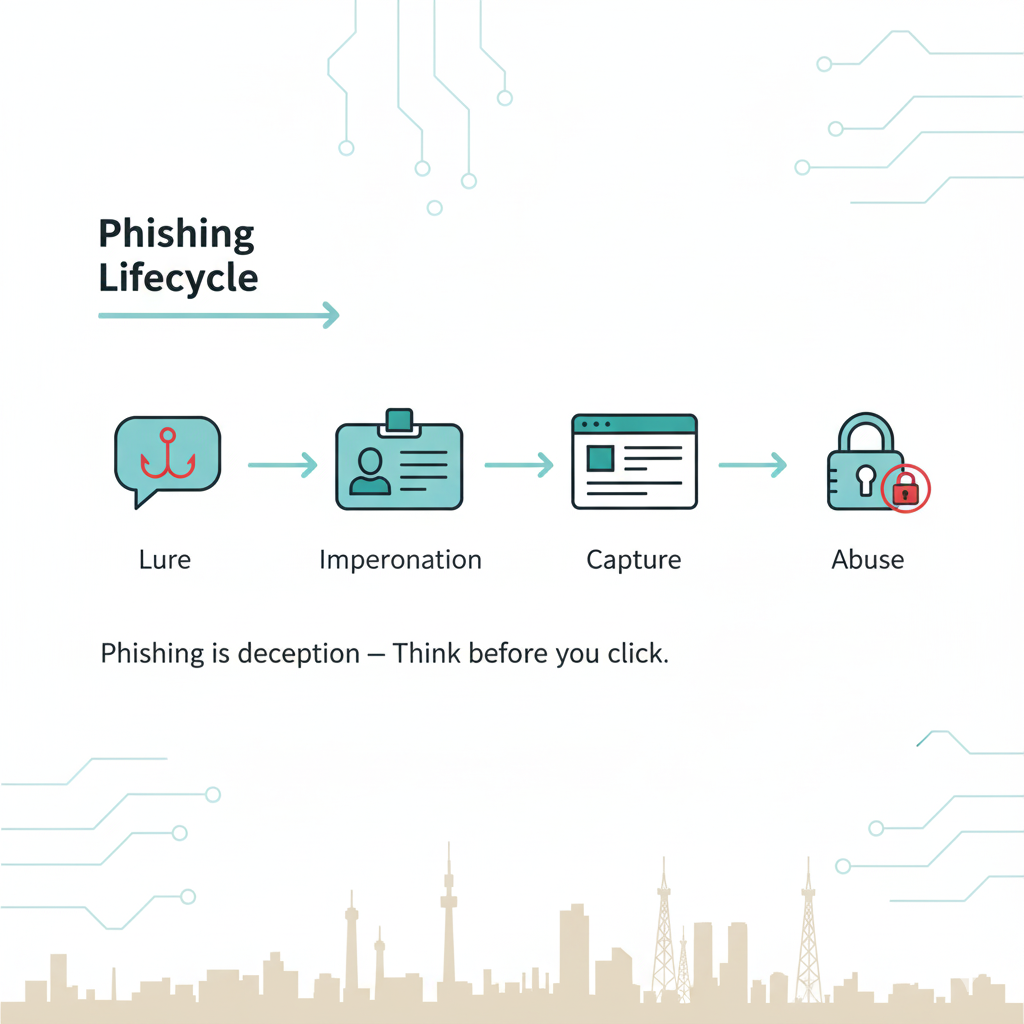
Lure: A message creates urgency or curiosity (payment problem, prize, job, verification).
Impersonation: Sender pretends to be a bank, telecom, government office, or partner NGO.
Capture: You’re pushed to click a link, enter a code/password, or open a file.
Abuse: Attackers log in to your accounts, steal funds/data, or spread to your contacts.
3) Common scenarios in Somalia
Mobile-money code theft (EVC/ZAAD): “We sent you money by mistake—share the code to reverse.”
Fake page verification (Facebook/Instagram/X): “Your page violates policy—verify in 24h” with a phishing form.
NGO/Job scams: “Shortlisted—open attachment or pay a fee to confirm interview.”
WhatsApp/Telegram account takeover: “Send me the 6-digit code to confirm.”
Government/utility impersonation: “Tax/utility arrears—pay now or service cut.”
4) Red-flag checklist (quick scan)
Urgent, threatening tone; gift or grant promises.
Sender address/number slightly off (typos, strange domains).
Links that don’t match the supposed organization.
Requests for passwords, OTPs, or mobile-money codes (legitimate orgs never ask).
Unexpected attachments (especially .html, .htm, .exe, macro-enabled Office files).
5) What to do if you receive a suspicious message
Don’t click. Don’t reply. Don’t forward.
Verify on a second channel: call the organization using the number on its official website, not the one in the message.
Preview links safely: hover on desktop; on mobile, long-press to see the real URL (don’t open if unsure).
Report and delete (see Section 8).
6) If you already clicked or shared a code/password
Immediately change the password for that account and any account using the same password.
Enable 2-Step Verification (app or hardware key; avoid SMS where possible).
Revoke sessions: log out of all devices/sessions in account security settings.
Check transactions: contact your bank/telecom provider for account freezes or chargeback options.
Scan your device with reputable antivirus; update your OS and apps.
7) Prevention for individuals & teams
Use a password manager to generate unique passwords.
Turn on 2FA for email, cloud, social, banking, and admin panels.
Keep devices and apps up to date; enable auto-updates.
Learn to inspect senders and URLs; when unsure, verify with a phone call.
For CSOs: run quarterly phishing drills, and create a simple internal reporting channel (e.g., security@yourorg.so
).
8) Reporting pathways (practical)
Platform: use in-app “Report” (Facebook/Instagram/X/WhatsApp/Telegram).
Telecom/Bank: call official support to flag fraud and protect mobile-money accounts.
Organization: inform your IT/security focal point immediately.
Law-enforcement: where appropriate, lodge a report with local cybercrime units.
9) Sample awareness snippets (you can reuse)
SMS/WhatsApp tip (English):
Never share one-time codes or passwords—no bank, telecom, or NGO will ask for them. Verify requests by calling the official number on the website.
Email banner (English):
Think before you click: hover to check the real link, and report suspicious emails to security@yourorg.so
.
10) Minimal policy controls for institutions
Enforce 2FA by default for staff email and admin accounts.
Deploy SPF, DKIM, and DMARC on your domain to reduce email spoofing.
Centralize updates and endpoint protection on staff devices.